Background
Shodan is an Open Source Intelligence (OSINT) tool used for tracking security flaws in networked hardware and software and any IOT device available via the Internet. At the beginner level, Shodan is a search engine for all sorts of services and vulnerabilities, including control systems, insecure baby monitors, security cameras, medical equipment, and whatnot. Shodan can access whatever is available on the Internet and dish out results that are programmer friendly and useful for those in the security community. You can explore Shodan’s Google-like web-based search interface at www.shodan.io.
Fun Fact: The name Shodan is inspired from SHODAN (Sentient Hyper-Optimized Data Access Network), the malevolent AI from the “System Shock” video game series that becomes self-aware and seeks to exert its influence over the digital and physical world.
You can do some pretty powerful stuff using the web interface. For instance, if you search for terms like…
netcam
port:3389
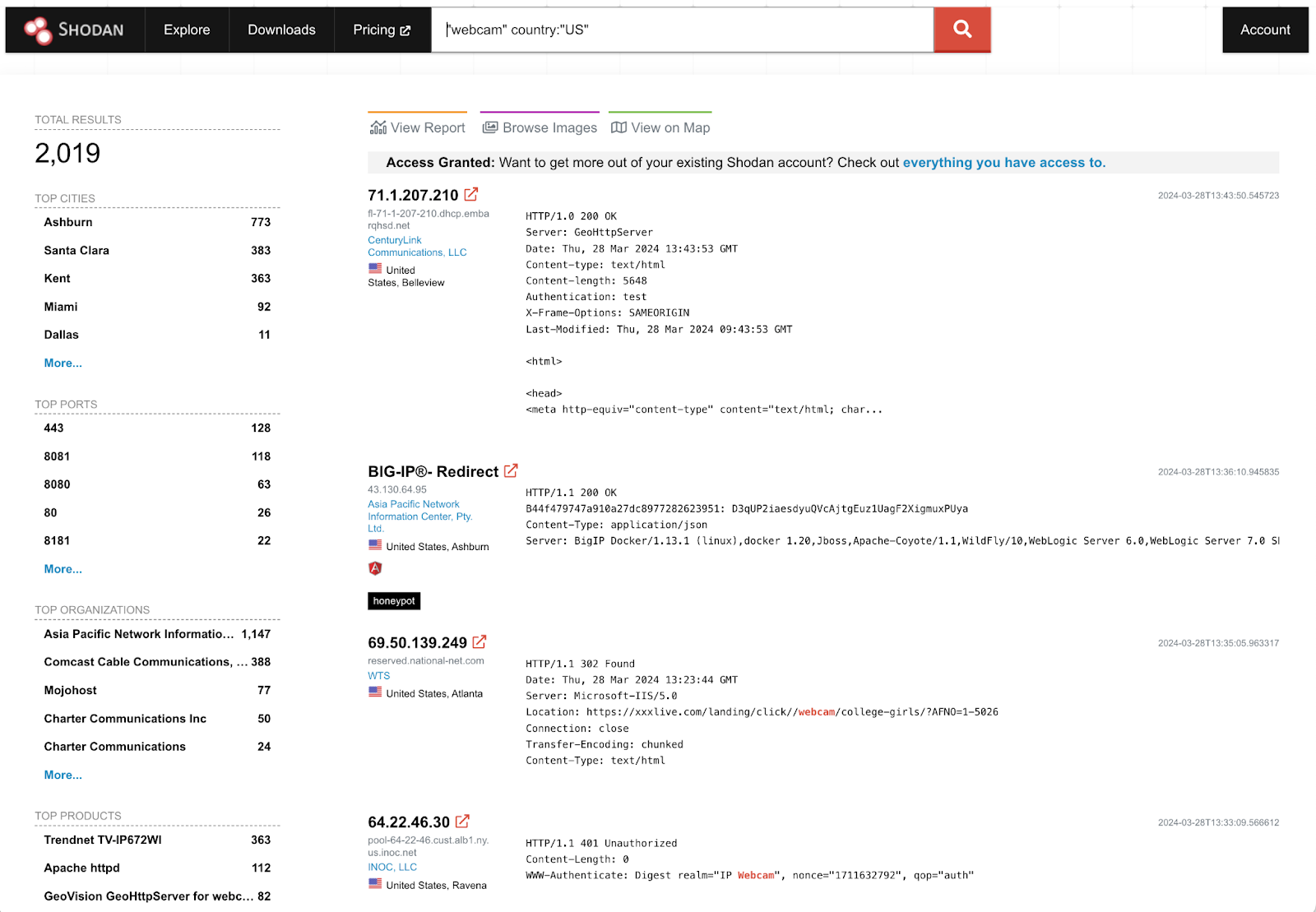
"webcam" country:"US"… it will return pages of results – once you register for an account.
Beyond a search engine, Shodan is available via APIs or CLI in programmable and scriptable developer-friendly ways to provide threat intelligence and enrichment. For example, you can query for what services and vulnerabilities there are on any given public IP and get the domain context, port information, hostname(s), ASN, ISP, geo-location information, etc.
Shodan CLI and python scripting for Security Researchers
Whether you are a security analyst, a devops engineer, or a developer, it is quite likely you love the command line – and will love the Shodan CLI. If you prefer not to venture beyond web consoles, you can still get good value from the Google-like web interface at www.shodan.io.
Shodan is also available as a python package. Check out the REST API toolkit on github at https://github.com/achillean/shodan-python. To use it, you will need to register and get an API key.
$ pip install shodan
$ shodan init <your_api_key>Now that it is installed, this is how you can use it:
$ shodan --help
Usage: shodan [OPTIONS] COMMAND [ARGS]…
Options:
-h, --help Show this message and exit.
Commands:
alert Manage the network alerts for your account
convert Convert the given input data file into a different format.
count Returns the number of results for a search
data Bulk data access to Shodan
domain View all available information for a domain
download Download search results and save them in a compressed JSON…
honeyscore Check whether the IP is a honeypot or not.
host View all available information for an IP address
info Shows general information about your account
init Initialize the Shodan command-line
myip Print your external IP address
org Manage your organizations access to Shodan
parse Extract information out of compressed JSON files.
radar Realtime Map of some results as Shodan finds them.
scan Scan an IP/ netblock using Shodan.
search Search the Shodan database
stats Provide summary information about a search query
stream Stream data in realtime.
version Print version of this tool.Now let’s look at some uses relevant to analysts. Note that running the shodan command doesn’t require any administrative privileges on your machine.
Let’s get started with what we can find on any given host on the Internet:
$ shodan host 8.8.8.8
8.8.8.8
Hostnames: dns.google
City: Mountain View
Country: United States
Organization: Google LLC
Updated: 2024-03-12T09:59:57.882607
Number of open ports: 2
Ports:
53/tcp
53/udp
443/tcp
|-- HTTP title: Google Public DNS
|-- Cert Issuer: C=US, CN=GTS CA 1C3, O=Google Trust Services LLC
|-- Cert Subject: CN=dns.google
|-- SSL Versions: -SSLv2, -SSLv3, -TLSv1, -TLSv1.1, TLSv1.2, TLSv1.3Beyond basic network and geo-information, Shodan gave me an idea of what ports and services are available on that host. You can also find what shows up for your home/home office’s public IP. First, get your public IP from https://www.whatismyip.com/.
$ shodan host <myip>Hopefully you don’t get any surprises there. Go after your teenage kids or your security agnostic mom if anything seems out of the ordinary. Cover both extremes!
Now let’s get into something that might surprise you. Let’s look for where we can find Windows RDP (default port 3389) running on the Internet:
$ shodan stats port:3389
Top 10 Results for Facet: country
CN 1,509,953
US 1,182,478
DE 193,177
JP 111,853
HK 104,659
NL 104,318
GB 96,448
SG 93,943
IN 67,265
FR 63,817
Top 10 Results for Facet: org
Tencent cloud computing (Beijing) Co., Ltd. 468,534
Google LLC 395,135
Tencent Cloud Computing (Beijing) Co., Ltd 311,209
Aliyun Computing Co., LTD 305,674
Microsoft Corporation 176,886
Incapsula Inc 150,133
Amazon Technologies Inc. 97,500
Asia Pacific Network Information Center, Pty. Ltd. 61,191
Huawei Public Cloud Service (Huawei Software Technologies Ltd.Co) 53,829
Incapsula Inc. 51,126So, how did it work? With Shodan, you are not actively scanning. Rather, you are querying against the database of information provided by Shodan’s passive scanning and indexing of the Internet. Shodan intermittently crawls and uses distributed low and slow scans, and then indexes in its big data store. Similar to how Google crawls the Internet to create a search index.
Because of this architecture, Shodan is incredibly powerful. When put to legitimate use, we can easily get an idea of what a rich variety of protocols and custom devices the Internet uses of late. Refrigerators, traffic lights, GPS devices, webcams, routers, switches, and so on. It amazes me the amount of webcams that allow public access!
The Shodan database lets you query by various attributes, including software name, version, port, IP, and other keywords. For example, let’s say you want to look for nginx webserver instances of a particular version, maybe because it is vulnerable.
You can use the shodan count command followed by the relevant query:
$ shodan count nginx 1.24.0
595391The command queried the Shodan database for servers with banners that contain information indicating they are running nginx version 1.24.0.
Now let’s make it a bit more useful. How about knowing the organization, hostname, IP, and port where these servers are running?
$ shodan search --fields ip_str,port,org nginxAt this point, you will get:
Error: Access denied (403 Forbidden)This is where the free ride ends. If you were willing to move up to the paid key tiers, you would get something like this response listing the IPs and the organizations (only pasting partial results here):
51.158.116.117 80 Dedibox SAS
54.213.34.119 80 Amazon.com
163.197.89.74 80 Citis Cloud Group Limited
45.39.60.186 80 EGIHosting
106.52.40.96 82 Tencent cloud computing
46.101.102.221 80 DigitalOcean
83.217.90.203 8888 Combell NV
54.36.100.11 81 OVH SAS
192.101.241.114 80 ColoMX LLC
101.206.210.191 9000 China Unicom Liaoning
5.145.175.201 80 Comvive Servidores S.L.
160.121.159.199 80 Clayer Limited
185.25.117.240 80 Hosting Ukraine LTD
152.32.185.170 80 Ucloud Information Technology (hk) Limited
193.27.6.240 80 Krajowa Izba Rozliczeniowa S.A.
18.166.210.203 82 Amazon.com
18.138.148.43 80 Amazon.com
103.94.137.195 80 Alliance Broadband Services Pvt.
3.87.238.11 80 Amazon.com
34.235.164.200 80 Amazon.com
156.250.201.73 9099 Power Line Datacenter
188.130.25.23 80 CTS Computers and Telecommunications Systems SAS
88.208.60.39 80 DataWeb Global Group B.V.
8.131.55.216 88 Hangzhou Alibaba Advertising Co.,Ltd.
208.96.18.237 80 DataPipe
51.91.97.193 80 OVH SAS
23.238.232.242 9999 Psychz Networks
35.234.59.102 80 Google Cloud
………Yeah! Isn’t it amazing what OSINT can give you! Let’s look at how you can make it go further by doing some python programming.
Here is my python code that extracts IP addresses that were found to be running nginx servers:
import shodan
KEY=""
api = shodan.Shodan(KEY)
try:
results = api.search('nginx')
for res in results['matches']:
print('%s' % res['ip_str'])
except shodan.APIError as e:
print('Error: ', e)This is the output I received:
78.71.26.153
45.79.142.211
23.80.34.175
18.205.76.206
68.183.251.203
178.128.200.201
104.219.254.121
45.95.89.249
117.148.165.109
68.183.81.31
193.34.144.161
67.227.117.32
51.116.105.179
155.94.184.204
34.215.217.235
112.29.194.185
156.225.183.103
154.86.144.224
92.222.202.49
183.97.18.5
183.97.18.5
156.227.147.148
13.233.179.4
210.61.180.46
…I leave it to your creative interests on what further code you write to work with this list of IPs.
Security, Privacy, and Ethical Considerations
While Shodan provides valuable information for security research, network monitoring, and educational purposes, it also highlights privacy and security risks inherent with our expanding world of IOT. Devices and services that are not properly secured may inadvertently expose sensitive access and information. It’s essential for device owners and network administrators to be aware of their Internet-facing assets and to secure them appropriately. Shodan can help.
If nothing else, Shodan serves as a warning as to how easy it really is to gain illicit access to public devices, including hacking into webcam streams or operating electronic devices from unauthorized sources.
Shodan is a very effective tool for security professionals and developers. The power of its database and scans is limited only by our imagination. I hope it is used to fix security loopholes and issue guidelines to careless deployments worldwide. Please use it responsibly!
PS: Query recently integrated Shodan into our federated search platform to enrich federated search results with OSINT. In the process of exploring Shodan for the integration, I grew to love it more and more. It is a powerful and flexible tool that a programmer or an analyst can leverage in many ways. (I include programmer because Shodan can be used as a building block to create new solutions to solve interesting problems.) Let us know if you would like to try out the integration.