I am excited to announce that Query Splunk App 2.4 is now available on Splunkbase! With more and more user feedback, we have been making steady improvements to our Splunk App for federated search. This release makes the app more intuitive, easy-to-use, and powerful.
What is the Query Splunk App?
The Query Splunk App enables you to add any connected data source into Splunk – without increasing ingestion or compute expenses. Query expands Splunk’s data reach with all the data you need, including from data lakes, warehouses, object storage, or any other connected source with security-relevant and observability data to support your Security Data Operations use cases, and more. The Splunk app deploys Query capabilities into Splunk, so you can search data sources not connected to Splunk and see the results as part of your Splunk console search results. To know more about the Query Splunk App, go here.
What’s New?
A key goal of this release was to make it intuitive for new users to benefit from the power and flexibility of our federated search without needing a ramp up period. I am proud to say that our engineering team has achieved exactly that. Version 2.4 makes the app seamless to Splunk users in bringing them search results from remote data sources. The new features that make this possible are:
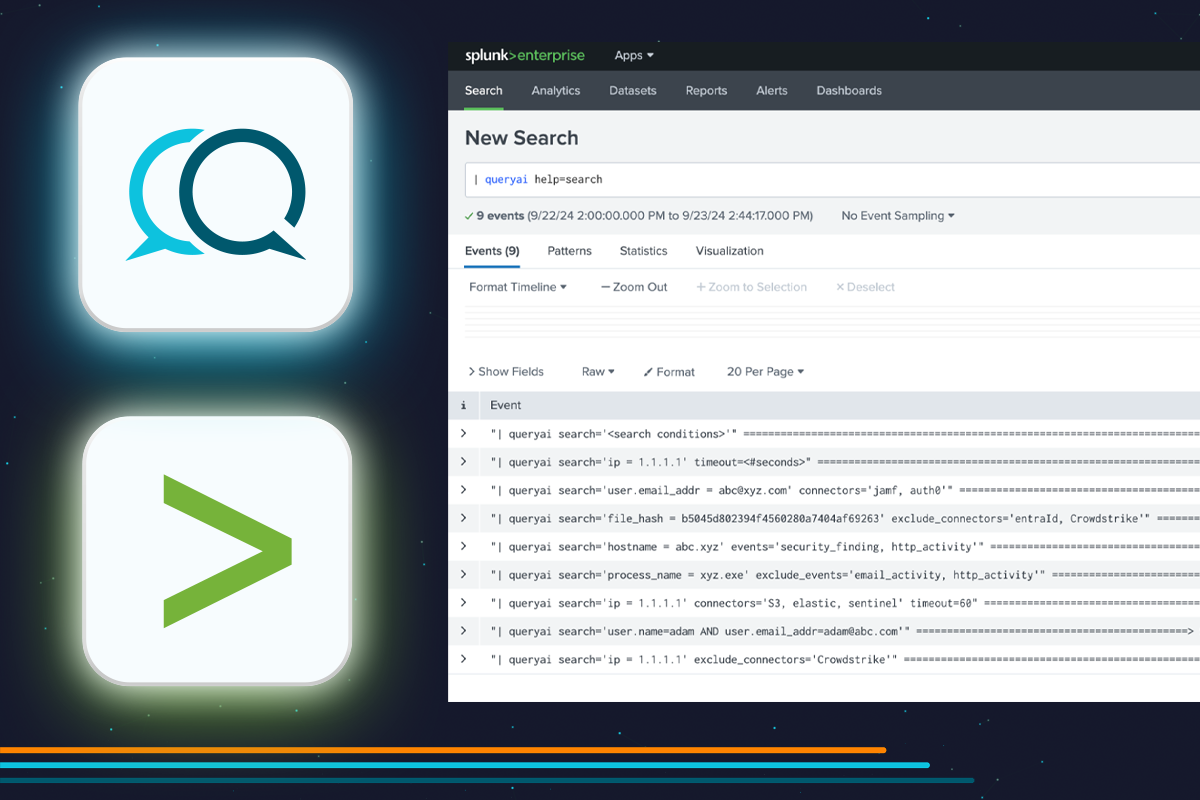
- Embedded help in the Splunk console with appropriate drill-downs for searching.
- Expanded breadth and depth of federated searching with ability to filter in/out by event classes. Try adding these new params
orevents=”system_activity, detection_activity”
for example, to your federated searches to see their effects.exclude_events=”file_activity” - Improved detection and handling of search errors. For example, if you mistype anywhere in
or if you set conditions on mismatched data types, we will alert you.file_activity.activity_id=ENCRYPT - Provided example searches to familiarize you and get you up and running faster.
- Updated schema as per the latest OCSF 1.3. (OCSF – Open Cybersecurity Schema Framework – is the open industry standard for security data schema.)
Another key goal was to make search meta-data easily available inside Splunk, so that users can quickly check:
- What connectors are configured to query data. Try running :
| queryai help=connectors - What entities can be searched. (Entities are key cybersecurity data types such as IP addresses, file hashes, etc.) Try running :
| queryai help=entities - What OCSF events and objects are available for searching. Try running :
| queryai help=events for example. - Any event or object schema to understand its attributes and relationships. For example, easily know that File System Activity event has an Activity attribute with values representing Create, Read, Update, Delete, Rename, Encrypt, Decrypt, Mount, Unmount, Open, … Also that it’s related to an Actor object and a Device object (via actor and device attributes).
Note: the example commands mentioned in above sections are able to be directly typed into Splunk Console’s search input.
This release also has a critical performance improvement that brings results faster and scales to show more data. You should definitely upgrade to 2.4 if you have run into any search timeouts.
The new Query Splunk App 2.4 release is now available on Splunkbase – just click here to get it. Contact us for more details or for help setting it up.