Detection coverage is constrained by ingestion.
That’s a heavy price to pay.
Modern environments generate valuable security telemetry across cloud platforms, SaaS apps, identity systems, security tools and more. Some of that data lands in a SIEM. A growing amount of it doesn’t — and never will.
When security detections depend on ingestion, coverage is limited. Data that never enters the system running detections effectively doesn’t exist, creating blind spots as a side effect of architecture.
Query separates detections from ingestion
Using the Query Security Data Mesh, detections run directly across your security data wherever it lives — including cloud services, SaaS platforms, security tools, object storage, data lakes, and SIEMs — without centralizing it first.
- Coverage expands to your data – wherever it is.
- Detection logic stays intact.
- Architecture stops dictating what you can detect.
Key Capabilities
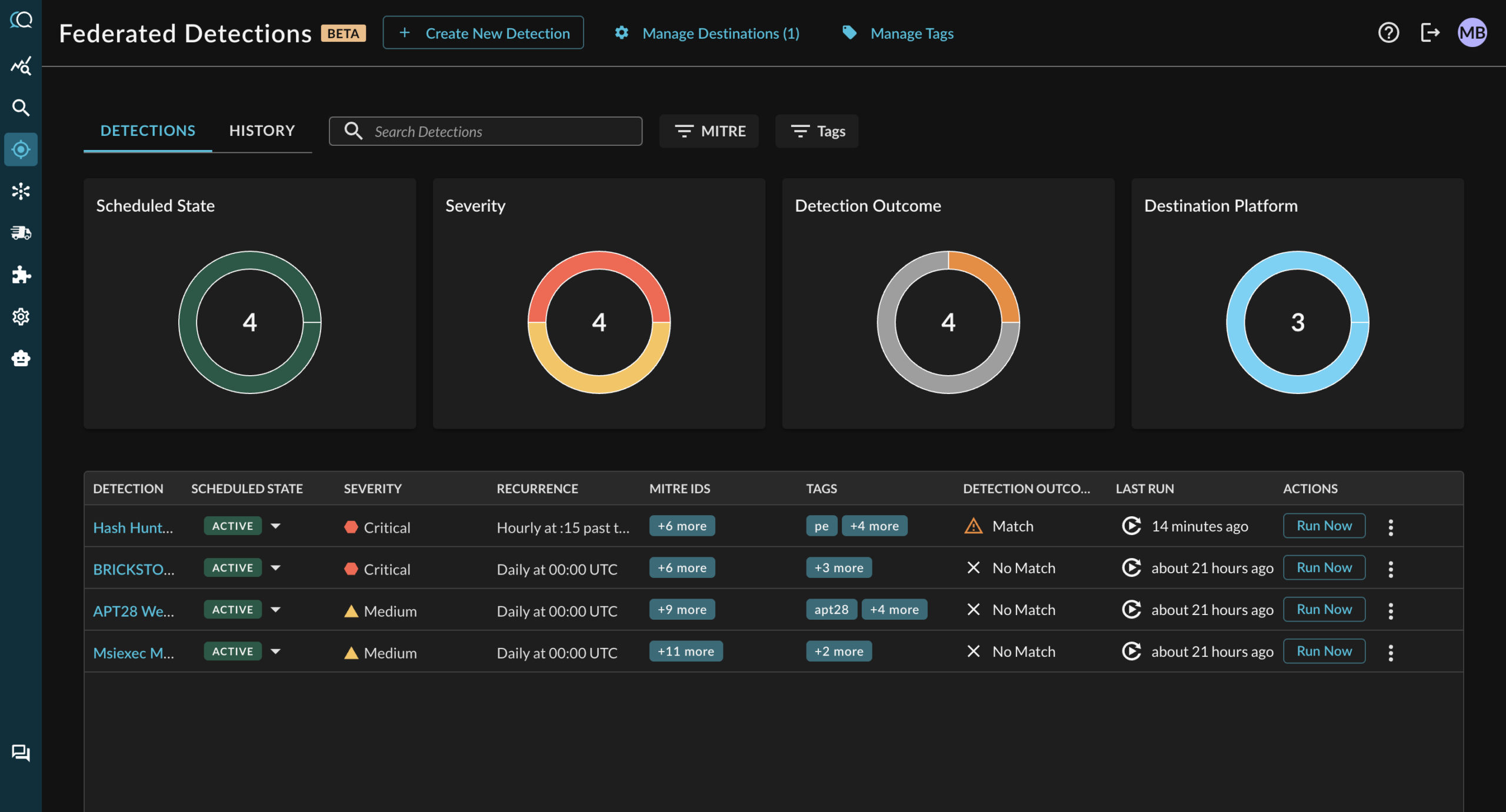
Run Detections Where the Data Lives
Federated Detections execute directly against distributed data sources — without ETL jobs, data duplication, or centralized storage.
If a data source is connected to Query, you can run detections against it.
Detection coverage without reshaping your data architecture
Structured Detection Logic
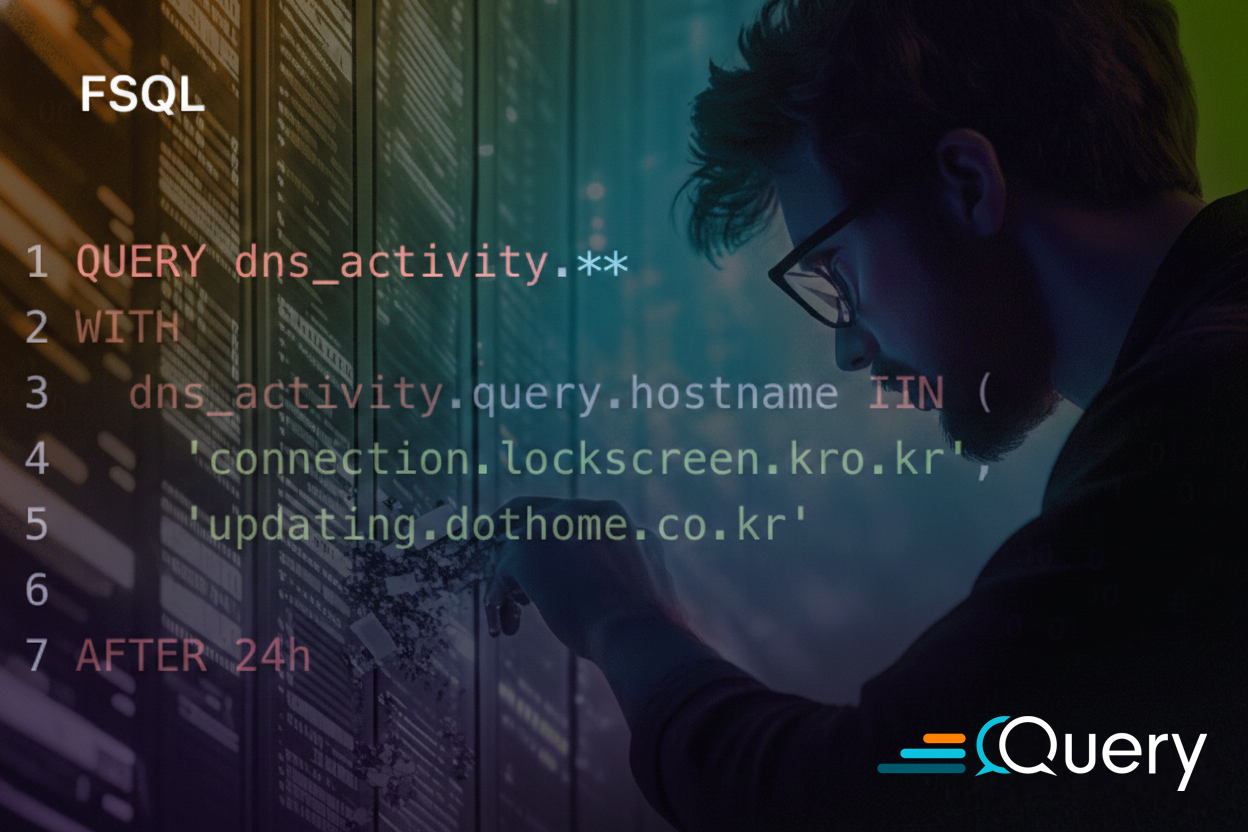
Define detections as scheduled queries written in Federated Search Query Language (FSQL) with explicit evaluation semantics.
Express logic teams rely on in production:
• Windowed aggregations and rates
• Grouping by users, identities, IPs, resources, or assets
• Threshold-based match conditions
High-signal detections that translate cleanly across sources
Deterministic, Scheduled Execution
Detections run on a defined cadence with explicit evaluation windows.
Each execution records the time range evaluated, source coverage, and match counts — so you know exactly what was checked and why a detection fired.
Detections you can reason about, audit, and trust
Efficient, Threshold-Driven Detection
Detections evaluate results against defined thresholds as they run and can terminate as soon as the condition is met.
This surfaces meaningful activity quickly — even across high-volume data — without waiting for a full scan when speed matters.
Faster signal in noisy environments, without unnecessary processing
Context-Rich Findings for Investigation
When a detection fires, Query provides a replay link that reruns the exact detection logic against the original time window. From there, analysts can:
• Review normalized results across contributing sources
• Pivot into related entities and events using federated search
• Continue the investigation wherever their judgment and experience lead
Faster understanding, deeper context, and investigations that don’t dead-end
Flexible Authoring and Migration
Detections can be authored directly in FSQL — or converted from existing detection logic. Query supports:
• Native FSQL authoring
• Translation from SPL, KQL, or Sigma
• Generating FSQL from natural language prompts
• Starting from proven detection recipes
This reduces the effort required to create, migrate, and maintain detections without rewriting everything on day one.
Faster adoption and broader detection coverage with less friction
A New Detection Architecture
Federated Detections run as scheduled queries across your connected security data, without centralizing or duplicating it.
Each detection evaluates data within a defined time window, applies threshold-based logic, and produces a deterministic outcome. When conditions are met, Query records the execution context and generates a finding.
Findings can be delivered to the chat, ticketing, and incident response tools you already use. Each includes a replay link that reruns the detection against the original time window, allowing analysts to explore normalized results and pivot freely as the investigation unfolds.
- No pipelines to manage.
- No ingestion dependencies.
- No handoff friction between detection and investigation.
What Changes with Federated Detections
- Broader detection coverage
Write rules once and run detections across all connected security data — including sources that don’t make sense to ingest into a SIEM. - Fewer blind spots as environments evolve
Coverage expands naturally as new data sources are connected, without reworking pipelines or logic. - Faster, more confident investigations
Replay-based findings and normalized results give analysts immediate context and freedom to pivot. - A more sustainable detection architecture
Detections no longer depend on ingestion decisions, reducing long-term operational friction as data volumes grow.